Setup overview
2025-12-16Last updated
Setting up Security Center SaaS involves planning, ordering, activating, and configuring the system.
- Learn about Security Center SaaS and how it works.
- Review the Security Center SaaS requirements:
- Commission a new system:
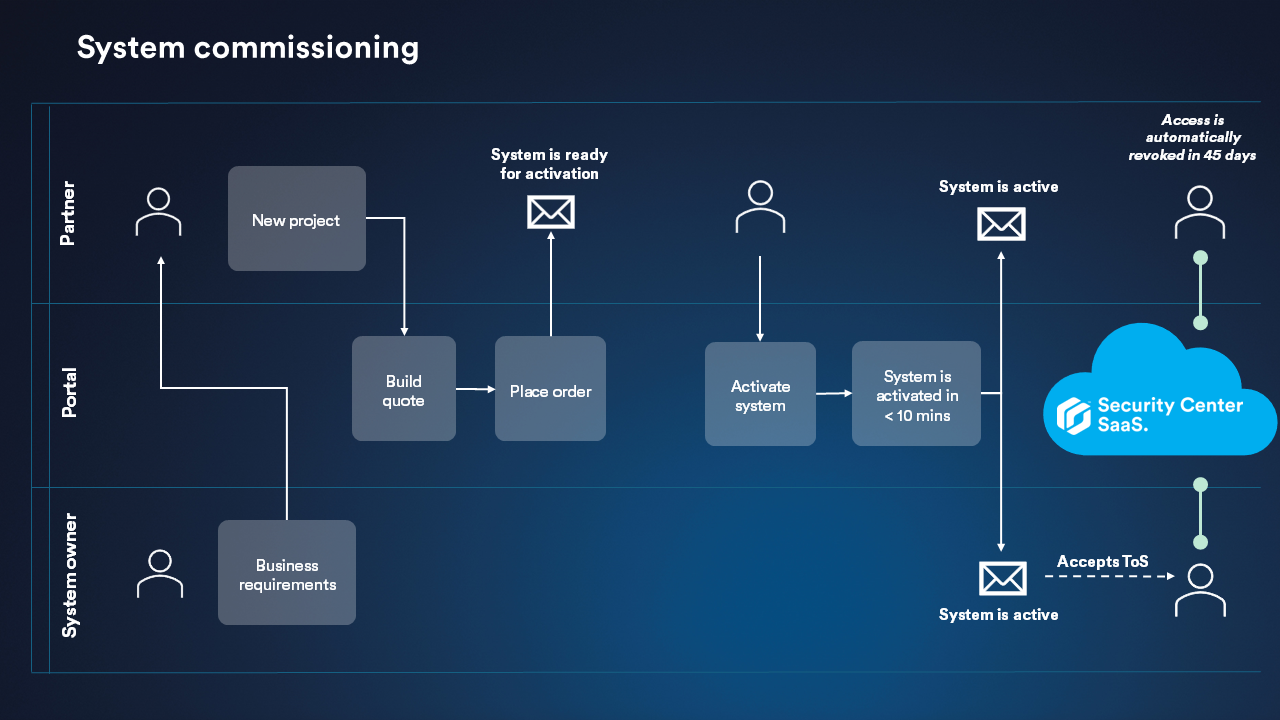
- Review the business requirements.
- Build a quote.
- Place an order.
- Activate the system.
- Sign in to Security Center SaaS.
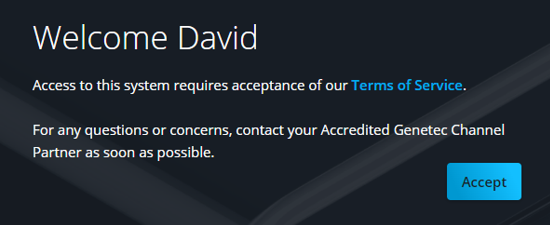
- Accept our Terms of Service.
 Important:During activation, the system integrator assigns access to selected users to configure the system. To grant access to additional users:
Important:During activation, the system integrator assigns access to selected users to configure the system. To grant access to additional users:- The end user system administrator specified on the order must sign in and accept the Terms of Service. If this step is not completed, assigned users can't sign in.
- An administrator must update the user group from the Access page of the target system in the System Management portal.
- Accept our Terms of Service.
- Create your users and apply roles.
- Create groups to define inherited user permissions based on group membership.
- Add devices.
- Activate video thumbnails on the timeline.
- Activate camera analytics events.
- Activate camera metadata.
- Activate privacy protection.
Note:The visibility of local devices depends on the location of your appliances. For devices to be discoverable, the appliance must be on the same local network as the device. - (Optional) Configure federation through reverse tunneling.
- (Optional) Download desktop clients from the Security Center SaaS Welcome page.
Watch this video to learn more. Click the Captions icon (CC) to turn on video captions in one of the available languages.
